Tekgem UNITY
Monitoring Cyber Security

What Is Tekgem UNITY?
Unity is a real time cyber security platform designed to complement and work alongside our physical health check and risk assessment.
The checks and assessments provided by Tekgem are incredibly valuable to assess your current environment, but what happens after Tekgem leave? Your environment is not static, you need to make changes, and as soon as you do there is the potential to introduce attack vectors.
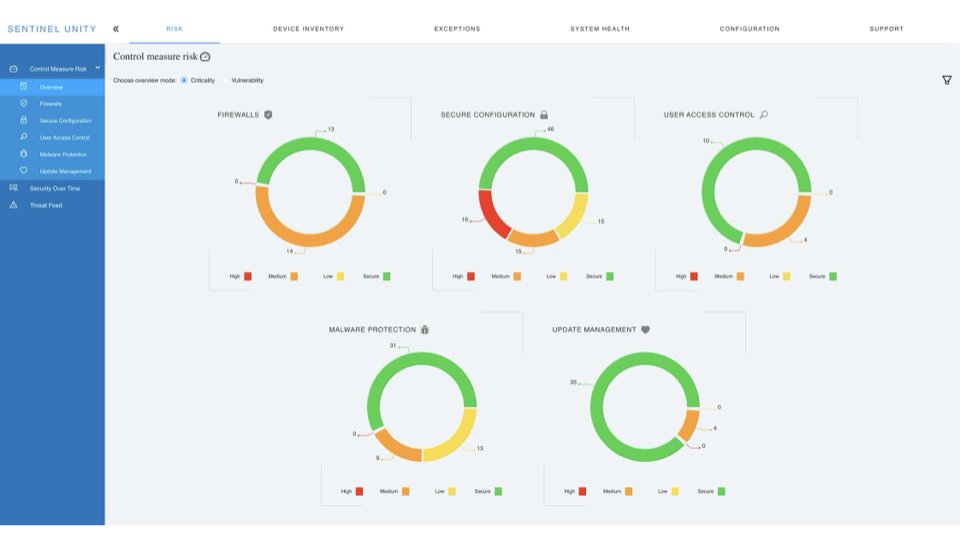
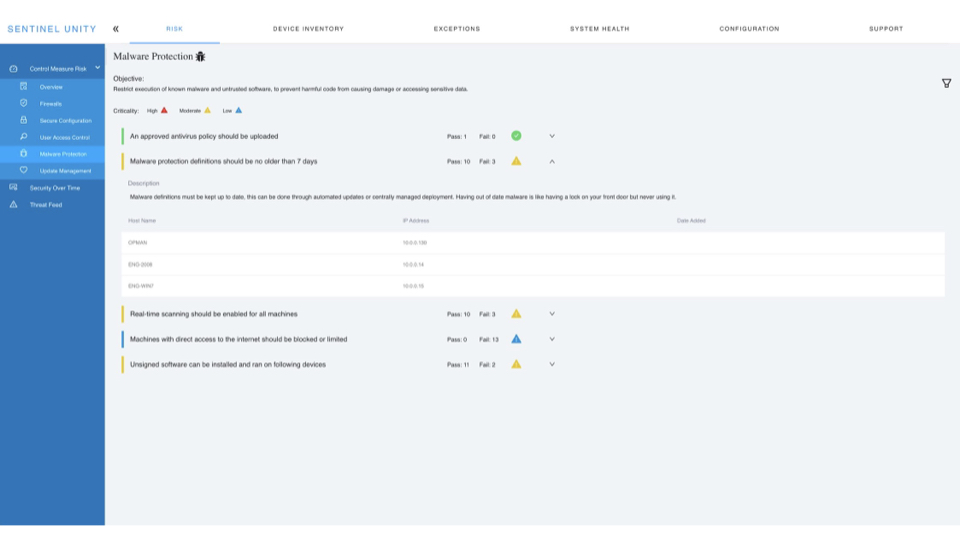
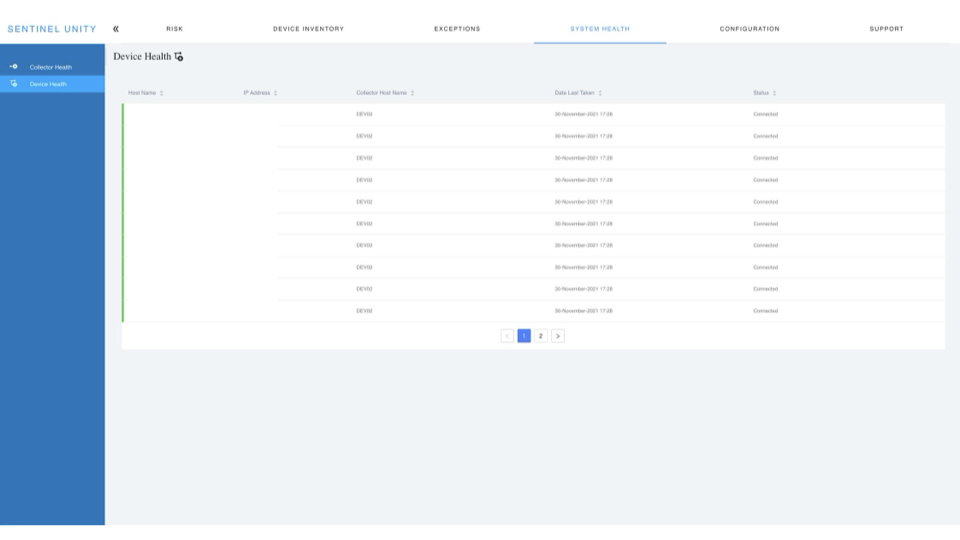
Unity is always on, and always checking the status of connected devices. If any device becomes insecure the industry standard security profile will flag it for attention immediately.
Unity ships with the Cyber Essentials risk profile, using it to provide essential monitoring of key vulnerabilities to help protect your network.
Who Is It For?
Unity was born from the need to protect operational technology (OT) and critical infrastructure and has been designed to do that from the ground up.
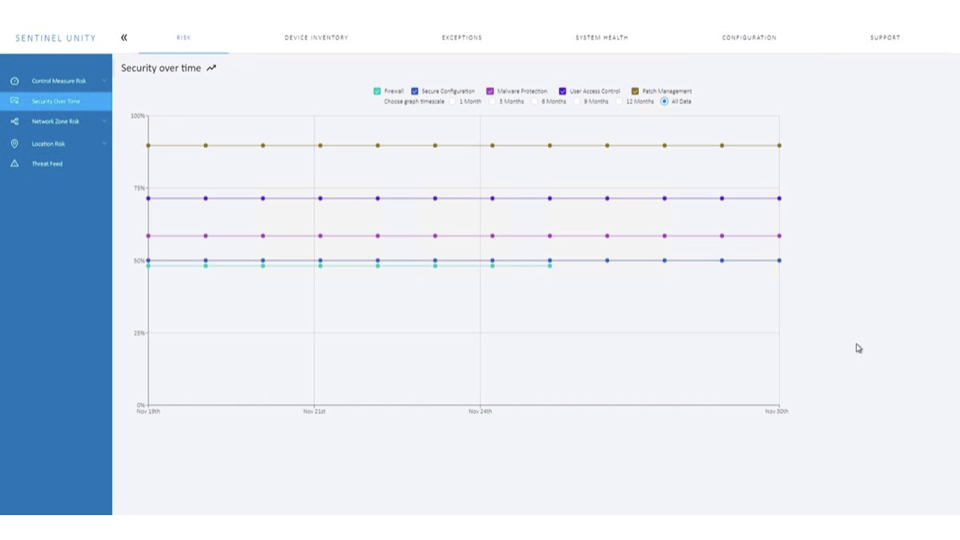
The regulated Process Industry (COMAH, NIS) are required by law to demonstrate they are managing their cyber security. Unity has particular benefits in this area, allowing you to demonstrate how your organisation has made improvements over time. As Unity is an extension of our existing services that are designed to support organisations its a perfect fit.
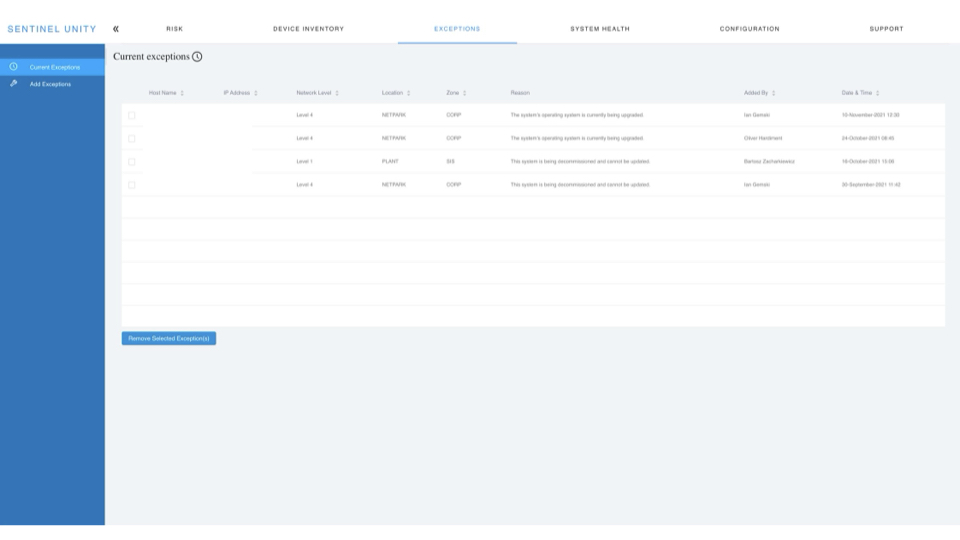
Any organisations without direct internet access on their network for security or logistical reasons will still benefit from Unity. Just because a network is not directly connected to the internet does not give it automatic protection. Any external device whether it’s removable media, a third party laptop or a vendor supplied system has the potential to introduce an attack vector. Unity takes air-gapped systems into account and offers a mechanism to ensure they are just as protected as all other parts of your network.
It can be used in any industry across any network. Unity sits in your OT network to help you visualise your level of vulnerability. If you have operational technology, then Unity will work for you 24/7.
Why Cyber Essentials?
Cyber Essentials is the starting point and foundation that all organisations should be familiar with and in control of. It’s designed to help protect your organisation against a whole range of the most common attacks.
By getting the basics right and ensuring you are fully compliant against that, you can move into true defence in depth with your security increasing that protection further.
Feature List
How Does It Work?
UNITY consists of two elements: the unity server – a central aggregation and visualisation tool, and Collectors – data gatherers.
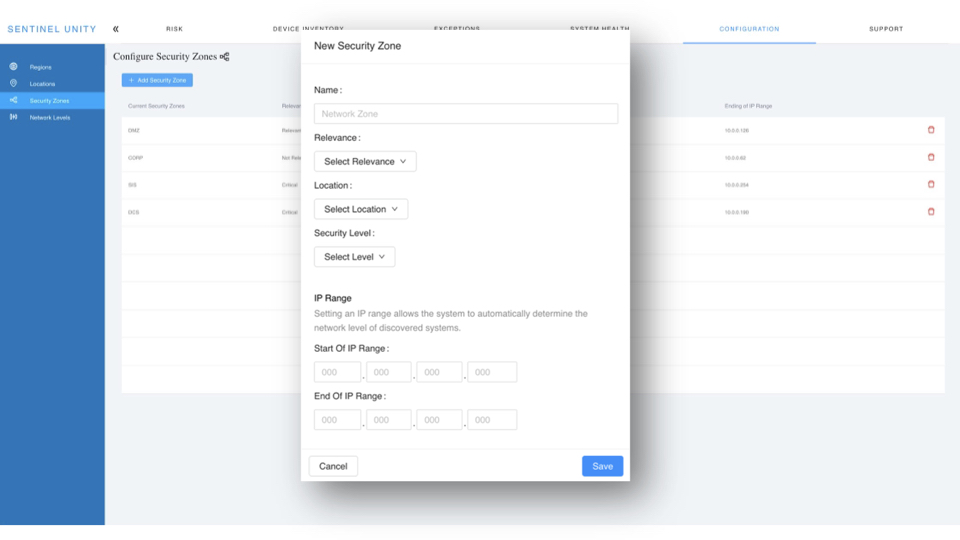
A ‘Collector’ is installed within each of your security zones to ensure maximum network coverage.
The Collector runs on a virtual server within that zone so is never installed onto any control system directly.
The Collector is designed to gather information from all systems within its security zone and pass it to UNITY which aggregates the data and presents it to you via the dashboard.